This site does not store any files on its server.We only index and link to content provided by other sites. In case of any query/objection regarding copyright or piracy, please inform us at hcbhatt@gmail.com.We will immediately respond to you. "Security is a culture"
Thursday, January 24, 2013
Tuesday, January 22, 2013
1-15 January 2013 Cyber Attacks Timeline
So here we are with the first Cyber Attacks Timeline for 2013 covering the first half of January.

Thursday, January 17, 2013
UPCOMING: Cisco Linksys Remote Preauth 0day Root Exploit
Story behind the vulnerability...
Months ago, we've contacted Cisco about a remote preauth (root access) vulnerability in default installation of their Linksys routers that we've discovered. We gave them detailed vulnerability description along with the PoC exploit for the vulnerability.
They said that this vulnerability was already fixed in latest firmware release... Well, not this particular vulnerability, since latest official Linksys firmware - 4.30.14, and all previous versions are still vulnerable.
Exploit shown in this video has been tested on Cisco Linksys WRT54GL, but other Linksys versions/models are probably also affected.
Cisco Linksys is a very popular router with more than 70,000,000 routers sold. That's why we think that this vulnerability deserves attention.
According to our vulnerability disclosure policy, the vulnerability details will be disclosed in following 2 weeks on http://www.defensecode.com/ , BugTraq and Full Disclosure.
Due to the severity of this vulnerability, once again we would like to urge Cisco to fix this vulnerability.
http://www.youtube.com/watch?v=cv-MbL7KFKE&hd=1
Facebook Malware campaign
We're seeing a massive campaign of malware distribution through Facebook look-a-like pages that started just before the new year.
T
hese pages are using the free DNS and hosting provider .tk. This provider has been used for many spam and malware campaigns in the past. Here are some of the domains used:
janejcfprofile.tk
natalieclolyu.tk
rosemaryrloveyouur.tk
sabrinadjoyys.tk
catherineufcitisfun.tk
rosemaryiiqsuper.tk
laurenaensweety.tk
carlyqwowdv.tk
So far, we've seen several hundred of such sites. They prompt the user to download a file with various names, such as:
YouWhoreGIF.exe
YouNiceJPG.exe
IamNiceBMP.exe
IamNicePNG.exe
YouFunnyJPEG.exe
IamLolBMP.exe
and may more
Only 1 AV vendor detects them as malicious at this time!
Looking at the source code, all the .tk domains load their content from another website through an IFRAME, with content from:
liwwh.eqeki.com
ngdy.hrdhm.org
lsmxz.totyn.net
cnpz.nukoq.com
...
These pages then redirect to a third URL on 208.131.138.217, hosting the malicious executable:
208.131.138.217/132.html
208.131.138.217/208.html
The malicious file is generated by http://208.131.138.217/imagedl.php.
As usual, do not run files downloaded on random Internet pages.
 |
| Malicious page distributing malware |
hese pages are using the free DNS and hosting provider .tk. This provider has been used for many spam and malware campaigns in the past. Here are some of the domains used:
janejcfprofile.tk
natalieclolyu.tk
rosemaryrloveyouur.tk
sabrinadjoyys.tk
catherineufcitisfun.tk
rosemaryiiqsuper.tk
laurenaensweety.tk
carlyqwowdv.tk
So far, we've seen several hundred of such sites. They prompt the user to download a file with various names, such as:
YouWhoreGIF.exe
YouNiceJPG.exe
IamNiceBMP.exe
IamNicePNG.exe
YouFunnyJPEG.exe
IamLolBMP.exe
and may more
Only 1 AV vendor detects them as malicious at this time!
Looking at the source code, all the .tk domains load their content from another website through an IFRAME, with content from:
liwwh.eqeki.com
ngdy.hrdhm.org
lsmxz.totyn.net
cnpz.nukoq.com
...
These pages then redirect to a third URL on 208.131.138.217, hosting the malicious executable:
208.131.138.217/132.html
208.131.138.217/208.html
The malicious file is generated by http://208.131.138.217/imagedl.php.
As usual, do not run files downloaded on random Internet pages.
Wednesday, January 9, 2013
Infrastructure Services 2013: Promote your value; Prevent their pain!
To understand
Follow the what comes out of the dumper with the name "Customer Needs".
 e
e Tuesday, January 8, 2013
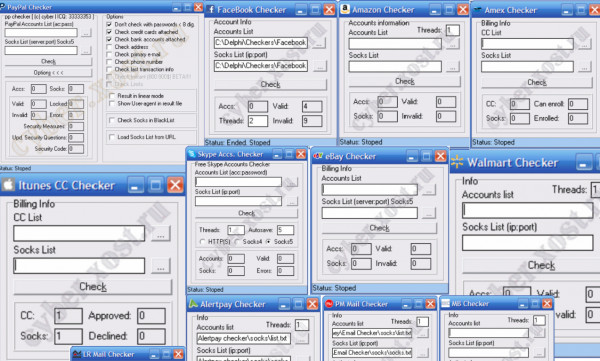
The Scrap Value of a Hacked PC
Computer users often dismiss Internet security best practices because they find them inconvenient, or because they think the rules don't apply to them. Many cling to the misguided belief that because they don't bank or shop online, that bad guys won't target them. The next time you hear this claim, please refer the misguided person to this blog post, which attempts to examine some of the more common -- yet often overlooked -- ways that cybecrcooks can put your PC to criminal use
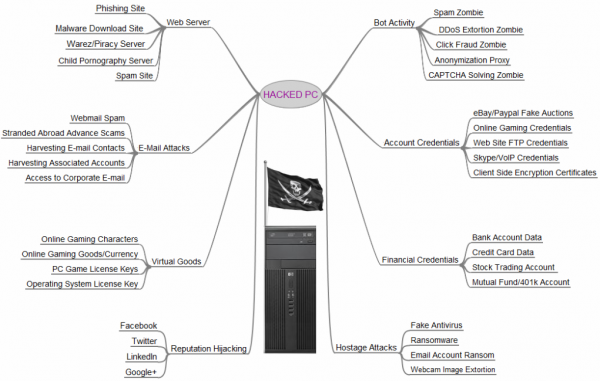 r
r
 r
r
This guy makes and markets dozens of account checking tools that are used to test the validity and status of many popular online stores and services, including Amazon, American Express, eBay, Facebook, iTunes, PayPal and Skype, to name a few.

Friday, January 4, 2013
Incident Response Checklist Actions
Incident Response Checklist Actions
A "mock" Incident Response Checklist using WMIC and a few other tools and attempt to answer the questions forensically so I am prepared when a real-world incident occurs (again).
1. Name of System and the Current Time:
C:\>hostname
WIN-xxxxxxxxx7
C:\>whoami
win-xxxxxxxxxx7\my name
C:\>echo %DATE% %TIME%
Fri 01/20/2012 20:52:34.28
C:\>wmic timezone list brief
Bias Caption SettingID
540 (UTC+09:00) Seoul
2. IP Address of the targeted system:
C:\>ipconfig /allcompartments /all
Windows IP Configuration
===============================================================
Network Information for Compartment 1 (ACTIVE)
===============================================================
Host Name . . . . . . . . . . . . : WIN-xxxxxxxxx7
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
Physical Address. . . . . . . . . : 00-00-00-00-00-00
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 192.168.1.151(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
NetBIOS over Tcpip. . . . . . . . : Enabled
3. Serial number of the system (this is going to be a bit off since I am on a Vmware instance):
C:\>wmic csproduct get name
Name
VMware Virtual Platform
C:\>wmic bios get serialnumber
SerialNumber
VMware-00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00
4. OS of the targeted system:
C:\>systeminfo | findstr /B /C:"OS Name" /C:"OS Version" - CREDIT
OS Name: Microsoft Windows 7 Ultimate
OS Version: 6.1.7601 Service Pack 1 Build 7601
C:\>ver
Microsoft Windows [Version 6.1.7601]
5. MAC Address of the system NIC:
C:\>wmic nicconfig get description,IPAddress,MACaddress
Description IPAddress MACAddress
Intel(R) PRO/1000 MT Network Connection {"192.168.1.151"} 00:00:00:00:00:00
RAS Async Adapter 00:00:00:00:00:00
Bluetooth Device (Personal Area Network)
----cut out some output----
6. How long has the system been online:
C:\>uptime.exe
\\WIN-xxxxxxxxxx7 has been up for: 0 day(s), 0 hour(s), 34 minute(s), 37 second(s)
7. Date and/or Level of Latest Patch:
C:\>wmic qfe get Hotfixid or if you wanted a bit more detail with dates C:\>wmic qfe list
HotFixID
KB971033
KB2305420
KB2393802
KB2425227
----cut out most of the output----
8. System Hardware:
C:\>wmic computersystem get manufacturer (assuming this would say, "Dell" if I was on a physical machine)
Manufacturer
VMware, Inc.
9. Software Installed on the System: I prefer wmic product list the best because it pulls install dates.
C:\>wmic product list
C:\>reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
10. Is there Anti-virus installed on the machine? If so, what brand and what are the latest anti-virus dat file updates? Were there any alerts?
I'm going to consider this one somewhat answered based off some of the information we already gathered from above, specifically: wmic get product list and running reg query against the Uninstall key. Other than that one could always look in the Uninstall Programs list to see if something is installed, or quite possibly look at the bottom right hand corner of the box and see if you see the "Shield" or another product logo. You could also see what's currently running as well. Some of the anti-virus vendors have unique process names.
11. Do you have EFS running on the system?
C:\>cipher /y
EFS certificate thumbprint for computer WIN-xxxxxxxxxx7:
0000 0000 0000 0000 0000 0000 0000 0000 0000 0000
C:\>cipher /s:"New Folder"
Listing C:\New Folder\
New files added to this directory will be encrypted.
E Meh.txt
E Foo.txt
E = Encrypted
12. Is there a firewall protecting the system? If so, do you have logs?
C:\>copy %windir%\System32\Logfiles\Firewall\*.log <output_directory>
C:\>netsh firewall show state
C:\>netsh firewall show config
C:\>netsh dump
Try these yourself. Too much information to paste here.
13. Is there any volatile network data?
C:\>route print
===========================================================================
Interface List
10...00 00 00 00 00 00 ......Intel(R) PRO/1000 MT Network Connection
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.1.1 192.168.1.143 10
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.1.0 255.255.255.0 On-link 192.168.1.143 266
192.168.1.143 255.255.255.255 On-link 192.168.1.143 266
192.168.1.255 255.255.255.255 On-link 192.168.1.143 266
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.1.143 266
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.1.143 266
===========================================================================
Persistent Routes:
None
------cut more output-------
C:\>arp -A
Interface: 192.168.1.143 --- 0xa
Internet Address Physical Address Type
192.168.1.1 00-00-00-00-00-00 dynamic
192.168.1.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 00-00-00-00-00-00 static
224.0.0.252 00-00-00-00-00-00 static
255.255.255.255 ff-ff-ff-ff-ff-ff static
C:\>netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 684
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 392
-----cut out most of the output-----
C:\>net start
These Windows services are started:
Application Information
Background Intelligent Transfer Service
Base Filtering Engine
Bluetooth Support Service
COM+ Event System
-----cut out most of the output-----
C:\>net user and C:\>wmic useraccount list
User accounts for \\WIN-xxxxxxxxxx7
---------------------------------------------------------------
Administrator Guest My Name
The command completed successfully.
C:\>net use
New connections will be remembered.
Status Local Remote Network
---------------------------------------------------------------------
Z: \\vmware-host\Shared Folders VMware Shared Folders
The command completed successfully.
C:\>type %windir%\System32\drivers\etc\hosts
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
C:\>type %windir%\System32\drivers\etc\networks
# For example:
#
# loopback 127
# campus 284.122.107
# london 284.122.108
loopback 127
14. Are there event logs?
C:\>wmic nteventlog get name - Use this output to create the next command
C:\>copy %windir%\System32\Winevt\Logs\*.evtx <output_directory>
Those were all of the questions asked on the incident response checklist I found online. My work one is much more detailed, but I don't have permission to release all of its contents nor will I get permission. I suggest all of you go through the "actionable" items so you're not surprised when an incident DOES occur (not IF).
Other "general questions" to ask in no particular order are:
Point of contact information.
What is the system used for?
What kind of information is stored on this system (Classified, PII, etc.)?
Is it public facing, or is it an internal system?
Is it a server or workstation?
Other Commands and Tools to run to collect information:
wmic process list status
wmic process list memory
wmic job list brief
wmic startup list brief
wmic ntdomain list brief
wmic service list config
handle.exe /accepteula
gplist
listdlls.exe
logonsessions.exe /accepteula
pslist.exe /accepteula
psloggedon.exe /accepteula
tasklist
tcpvcon.exe -a /accepteula
To My 13-Year-Old, An iPhone Contract From Your Dad, With Love
To My 13-Year-Old, An Smart Phone From Your Dad, With Love..
1. It is my phone. I bought it. I pay for it. I am loaning it to you. Aren't I the greatest?
2. I will always know the password.
3. If it rings, answer it. It is a phone. Say hello, use your manners. Do not ever ignore a phone call if the screen reads "Mom" or "Dad." Not ever.
4. Hand the phone to one of your parents promptly at 7:30 p.m. every school night and every weekend night at 9:00 p.m. It will be shut off for the night and turned on again at 7:30 a.m. If you would not make a call to someone's land line, wherein their parents may answer first, then do not call or text. Listen to those instincts and respect other families like we would like to be respected.
5. It does not go to school with you. Have a conversation with the people you text in person. It's a life skill. *Half days, field trips and after school activities will require special consideration.
6. If it falls into the toilet, smashes on the ground, or vanishes into thin air, you are responsible for the replacement costs or repairs. Mow a lawn, babysit, stash some birthday money. It will happen, you should be prepared.
7. Do not use this technology to lie, fool, or deceive another human being. Do not involve yourself in conversations that are hurtful to others. Be a good friend first or stay the hell out of the crossfire.
8. Do not text, email, or say anything through this device you would not say in person.
9. Do not text, email, or say anything to someone that you would not say out loud with their parents in the room. Censor yourself.
10. No porn. Search the web for information you would openly share with me. If you have a question about anything, ask a person -- preferably me or your father.
11. Turn it off, silence it, put it away in public. Especially in a restaurant, at the movies, or while speaking with another human being. You are not a rude person; do not allow the iPhone to change that.
12. Do not send or receive pictures of your private parts or anyone else's private parts. Don't laugh. Someday you will be tempted to do this despite your high intelligence. It is risky and could ruin your teenage/college/adult life. It is always a bad idea. Cyberspace is vast and more powerful than you. And it is hard to make anything of this magnitude disappear -- including a bad reputation.
13. Don't take a zillion pictures and videos. There is no need to document everything. Live your experiences. They will be stored in your memory for eternity.
14. Leave your phone home sometimes and feel safe and secure in that decision. It is not alive or an extension of you. Learn to live without it. Be bigger and more powerful than FOMO (fear of missing out).
15. Download music that is new or classic or different than the millions of your peers that listen to the same exact stuff. Your generation has access to music like never before in history. Take advantage of that gift. Expand your horizons.
16. Play a game with words or puzzles or brain teasers every now and then.
17. Keep your eyes up. See the world happening around you. Stare out a window. Listen to the birds. Take a walk. Talk to a stranger. Wonder without googling.
18. You will mess up. I will take away your phone. We will sit down and talk about it. We will start over again. You and I, we are always learning. I am on your team. We are in this together.
Subscribe to:
Posts (Atom)
